SAW - Hack The Box (htb) | 40 points
Challenge: SAW (HTB | Hack the box): 40 points
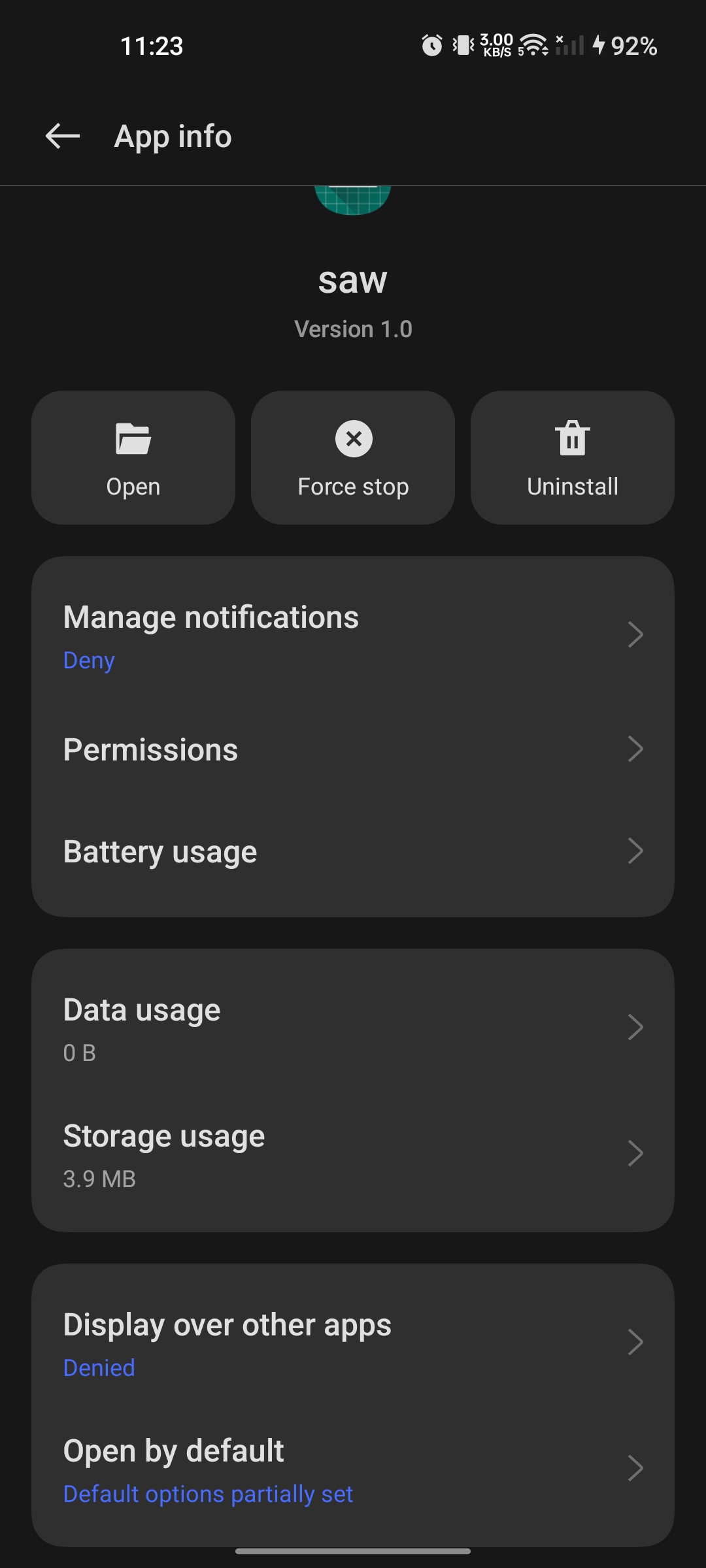
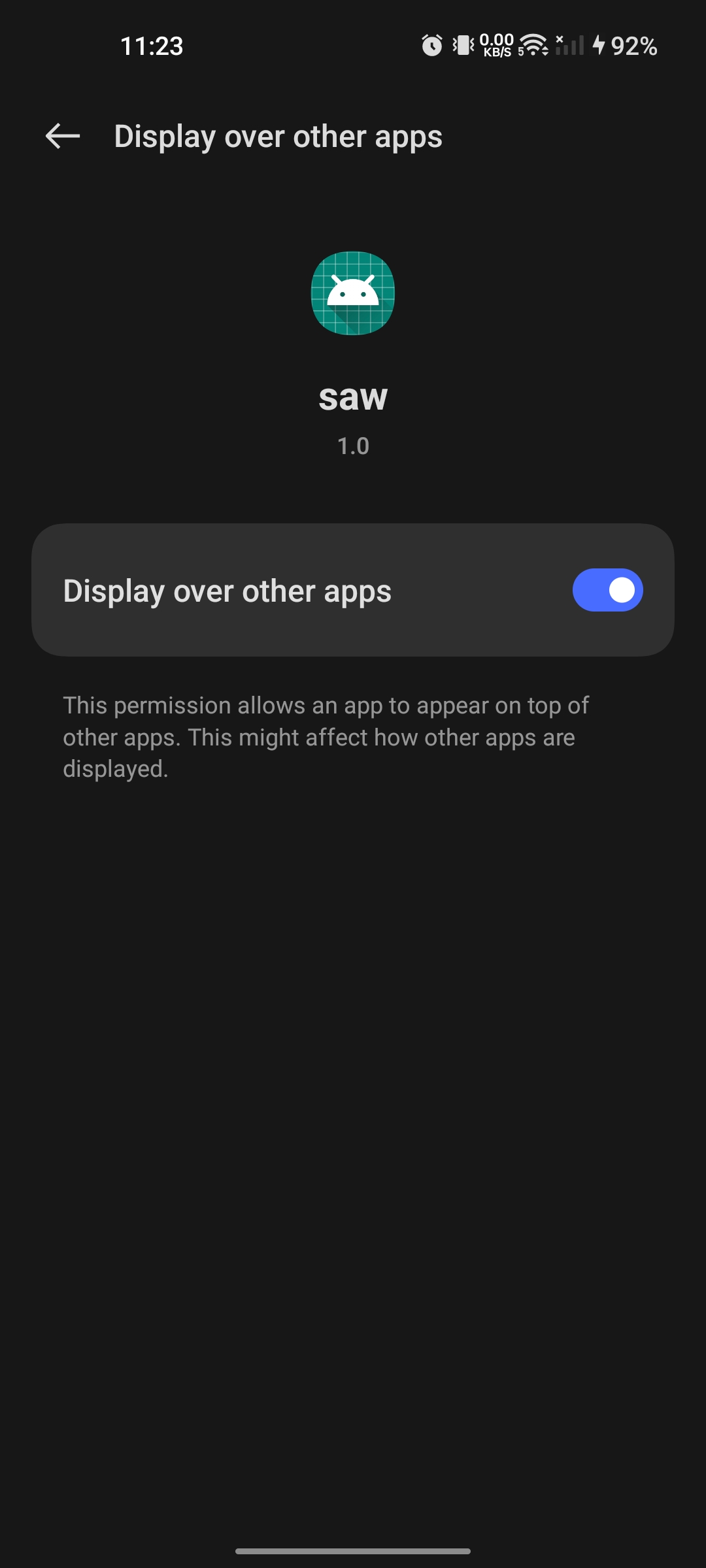
It was an easy but weird challenge. When you install the apk and try to open it, it’s not going to open. Initially I thought there was some permission issue, so I open the permissions settings and found only notification and display over other app in the setting. I thought that it was not relevant at all, so I moved on to check the code.
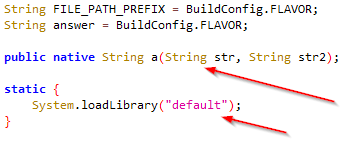
When you start analyzing the code, it’s the first thing you’ll notice that this app is using the nativ code somewhere.
It’s a nativ library default which is getting used by this app that can be found in the lib folder.
I moved ahead and analyze the code further.
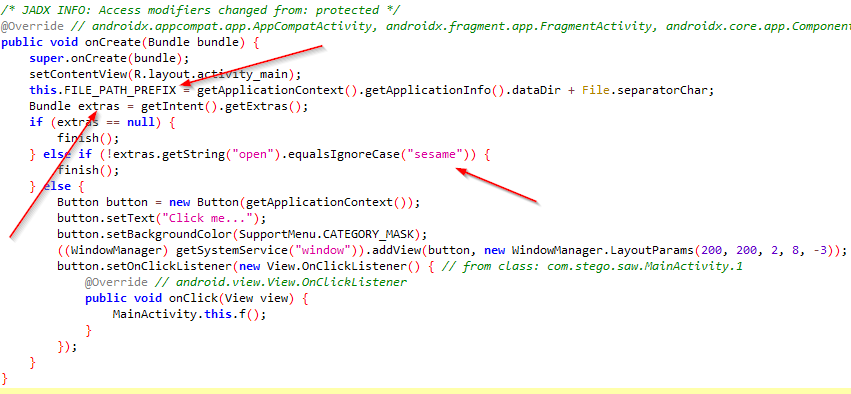
Next, you can see that the FILE_PATH_PREFIX variable has a package path, where some file must be saved and extras are expecting a string extra with the key "open" and the value is "sesame". It means we need to start the MainActivity activity with a extra value to pass on using intent. I searched through StackOverflow and found a way to use adb.
1
adb shell am start -a android.intent.action.MAIN --es open "sesame" -n com.stego.saw/.MainActivity
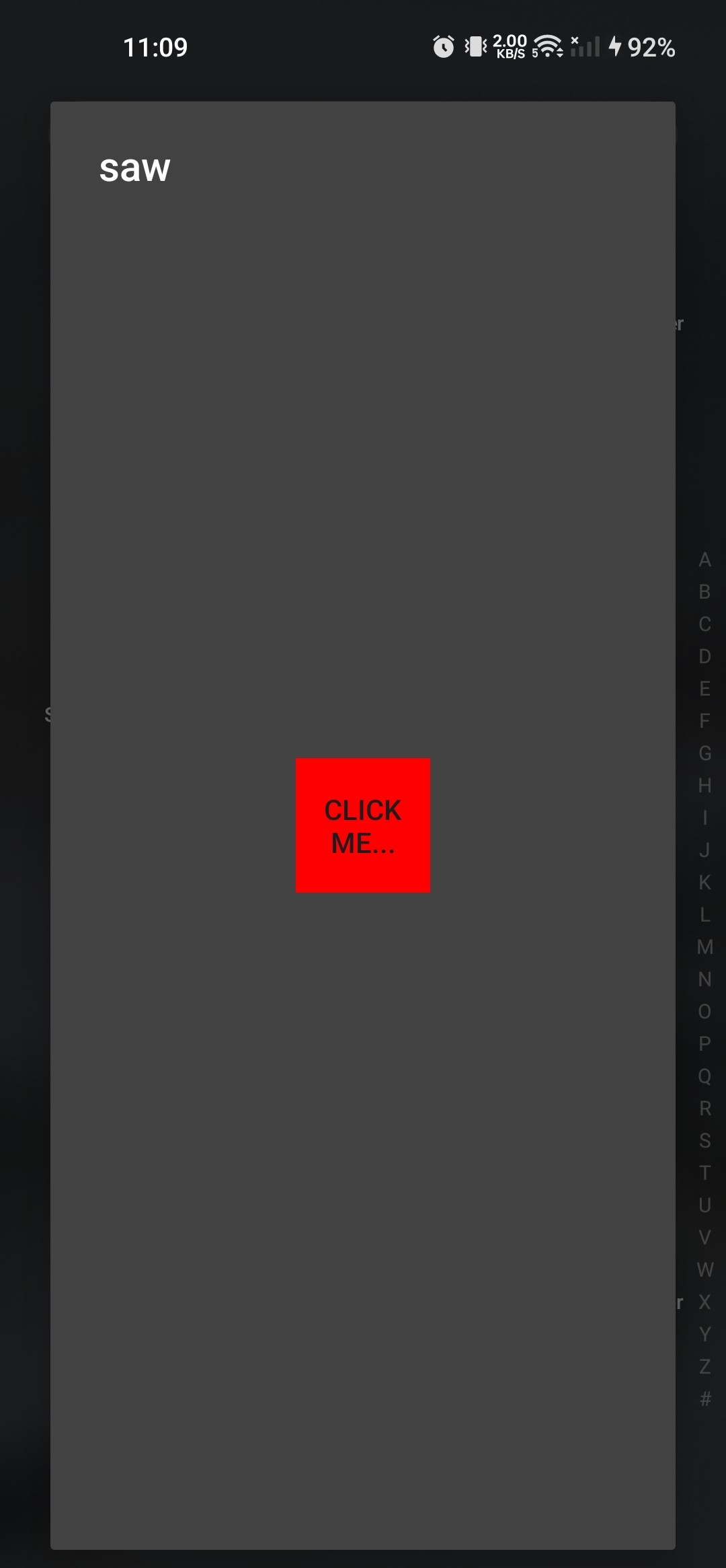
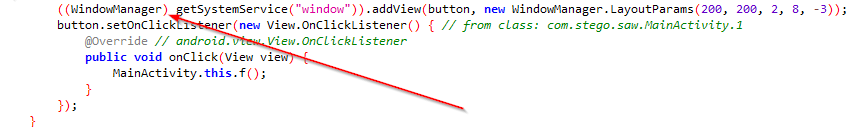
Now you can see the app is running, but when you click on the button click me... it will close again because I missed the important thing from the first analysis, which is, it’s creating a new window that will open app over other apps (“display app over other”). As I mentioned, there were 2 permissions when the app didn’t start. I gave it that permission.
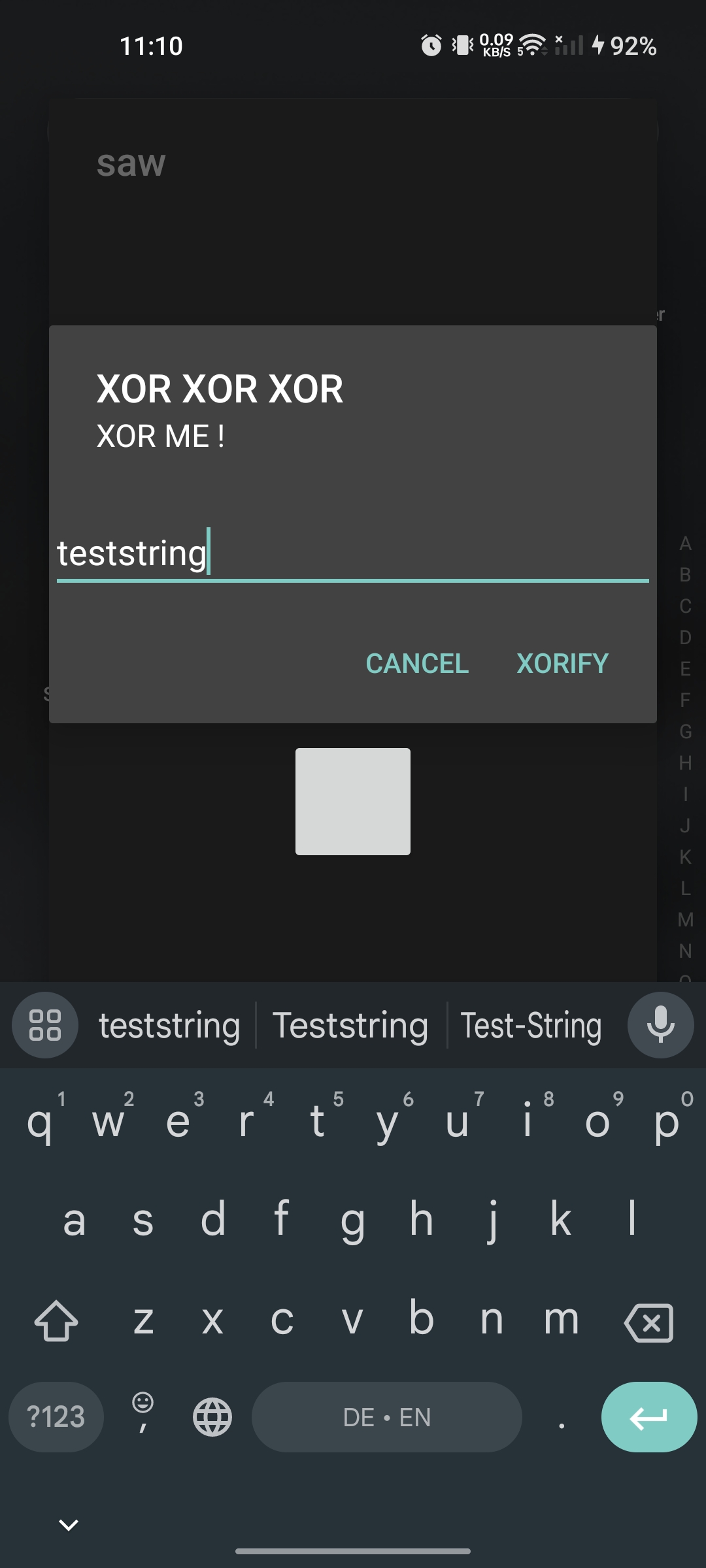
After restarting again, it worked. I clicked on the button, then it showed me a popup. I typed a random string and clicked XORIFY, which seemed like a bitwise XOR operation, but it also did nothing, and closed the popup.
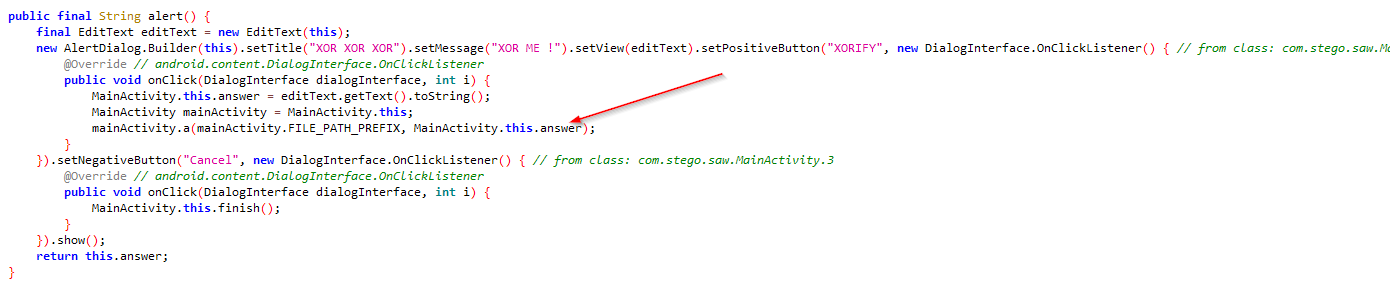
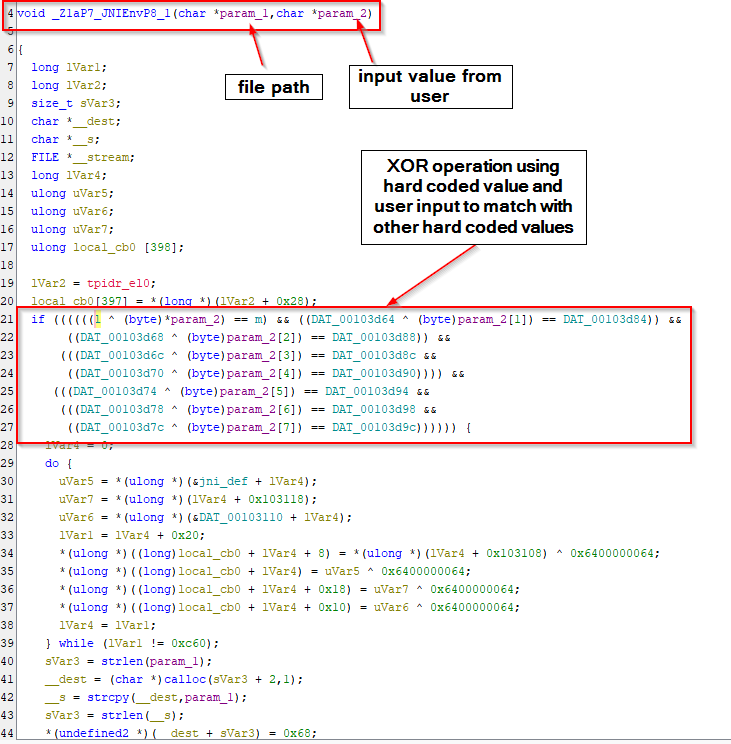
I then again moved to coding part to analyze further and found the last thing in the code, which is called the native library with two params. 1st param is the file path which we saw earlier, and the other one is the input we provides through the popup window.
It’s time to open and analyze the native code file. As soon as I opened and check for all the functions, I only saw one function which require two params as we saw earlier. I started to read it and found the XOR operation as it was mentioned in the popup window.
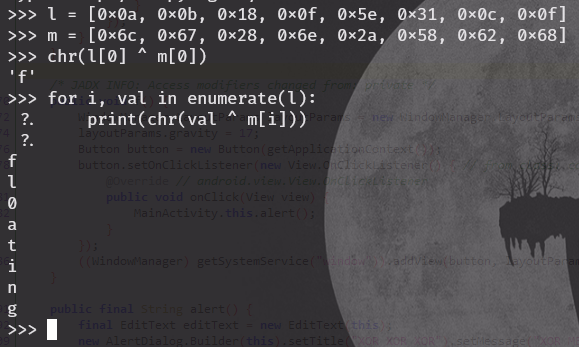
Input values were hard coded to do XOR opperation with variable l and compared against the variable m and it’s size was 8 character (did you see that the index 7 was the last index used to compare?). In other words, if l XOR input = m, input = l XOR m. This is where I started to check for values stored in l and m and found those.
I fired up the python console to check what the string was, and found it was fl0ating.
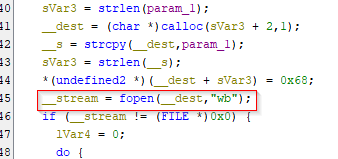
I started the app to try the string fl0ating. As we saw earlier, if that operation is a success, the native code is saving something in the file. As it was the last thing in the android code and in native code, I expected that file must contain something important.
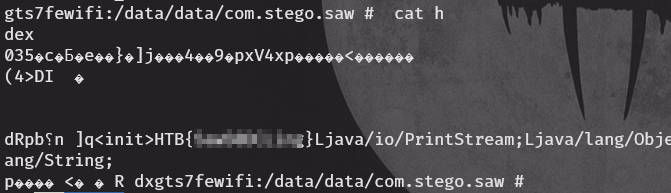
Also, as we know that the file path is inside the app package path, we need to go there and check what is going on. To get into the path, we must have a rooted device/emulator. Once you are inside the package path, you’ll see only one file name h. I just did cat and I found the flag there, although it appeared as a dex file.
And the question was solved. Happy hacking!
FLAG:
HTB{xxxxxxCLing}